Sylkie
/sel-kee/Spoofing IPv6 addresses using Neighbor Discovery
sylkie / GitHub
Created by Dan Robertson / GitHub
Why?
- Seemed like a good way to learn
- No known tool in existence
- Legitimate use cases for address spoofing
- Testing
- Intention to write a Router Advert Daemon that implements RFC 3971
Disclaimers
I am not an expert

Project is still in the very early phase of development.
commit 05c1f44ad0b0c63839a56ef2ffc73b08c69cfb9c (tag: v0.0.1)
Author: Dan Robertson <dan.robertson@anidata.org>
Date: Sun Jun 18 04:15:41 2017 +0000
Initial Commit - All the things!
Add all the things squashed up into one commit
A brief look at history
ARP
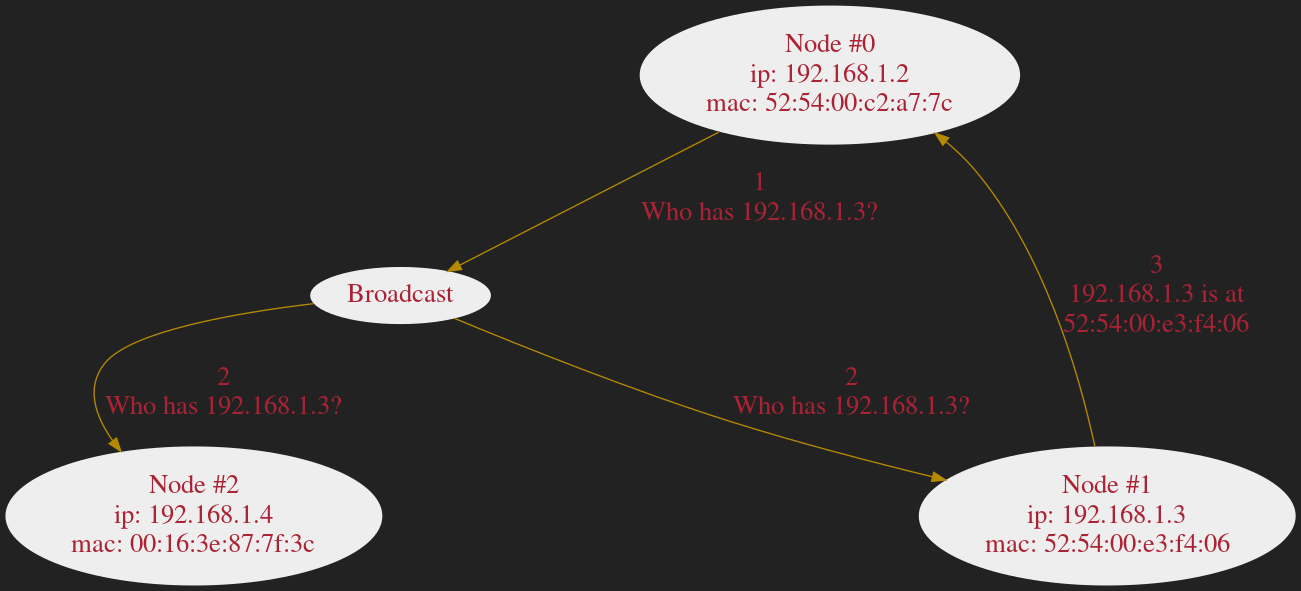
| Host | IP Address | Link-layer Address |
|---|---|---|
| Node #0 | 192.168.1.2 | 52:54:00:c2:a7:7c |
| Node #1 | 192.168.1.3 | 52:54:00:e3:f4:06 |
| Attacker | 192.168.1.3 | 00:16:3e:87:7f:3c |
ARP Spoofing
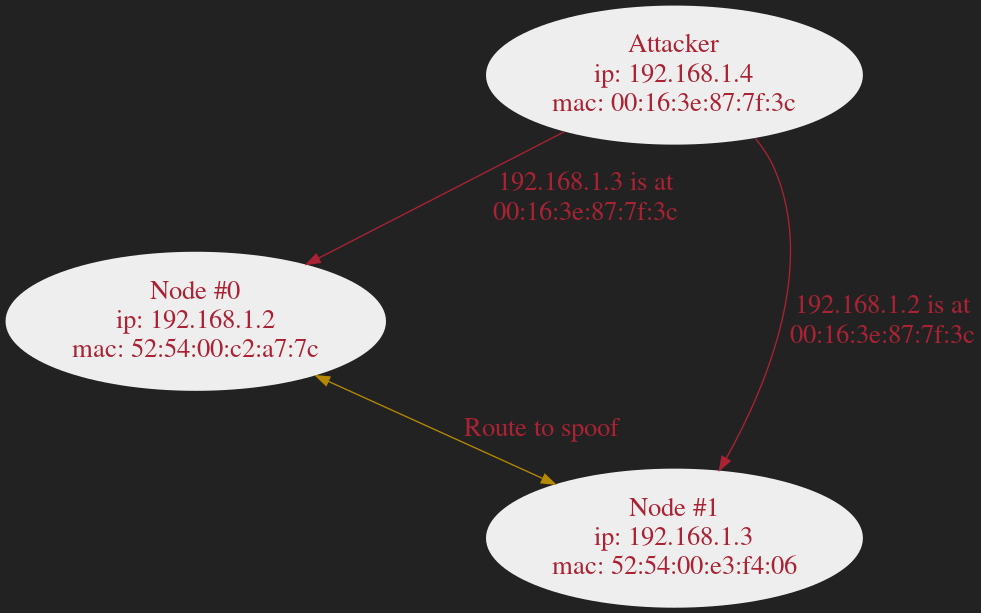
- Every machine on the LAN must examine every ARP request
- Possible for attackers to be off-link
- Stateless
IPv6 and Neighbor Discovery
How does it improve on ARP?
- More features
- On-link communication only
- Every machine on the LAN does not examine every request
- Builds on an existing protocol (ICMPv6)
Multicast Addresses
| 8 | 4 | 4 | 112 bits |
+------ -+----+----+---------------------------------------------+
|11111111|flgs|scop| group ID |
+--------+----+----+---------------------------------------------+
An IPv6 multicast address is an identifier for a group of interfaces (typically on different nodes). An interface may belong to any number of multicast groups.
| Address | Group |
|---|---|
| ff02::1 | All Nodes |
| ff02::2 | All Routers |
| 8 | 4 | 4 | 112 bits |
+------ -+----+----+---------------------------------------------+
|11111111|flgs|scop| group ID |
+--------+----+----+---------------------------------------------+
| Address | Multicast | Flags | Scope | Group |
|---|---|---|---|---|
| ff02::1 | ff | 0 | 2 | 1 |
| None | Link-Local | All-Nodes | ||
| ff02::2 | ff | 0 | 2 | 2 |
| None | Link-Local | All-Routers | ||
Solicited-Node Address
A Solicited-Node multicast address is formed by taking the low-order 24 bits of an address (unicast or anycast) and appending those bits to the prefix ff02:0000:0000:0000:0000:0001:ff
| fe80:0000:0000:0000:b95b:0ee1:cafe:9720 | |
| & | 0000:0000:0000:0000:0000:0000:00ff:ffff |
| = | 0000:0000:0000:0000:0000:0000:00fe:9729 |
| ff02:0000:0000:0000:0000:0001:ff00:0000 | |
| | | 0000:0000:0000:0000:0000:0000:00fe:9729 |
| = | ff02:0000:0000:0000:0000:0001:fffe:9729 |
Protocol Goals
- Router Discovery
- Prefix Discovery
- Parameter Discovery
- Address Autoconfiguration
- Address Resolution
- Next-hop Determination
- Neighbor Unreachability Detection
- Duplicate Address Detection
- Redirect
Five Message Types
- Router Advertisement
- Router Solicitation
- Neighbor Advertisement
- Neighbor Solicitation
- Redirect
Message Options
- Source Link-layer Address
- Target Link-layer Address
- Prefix Information
- Redirected Header
- MTU
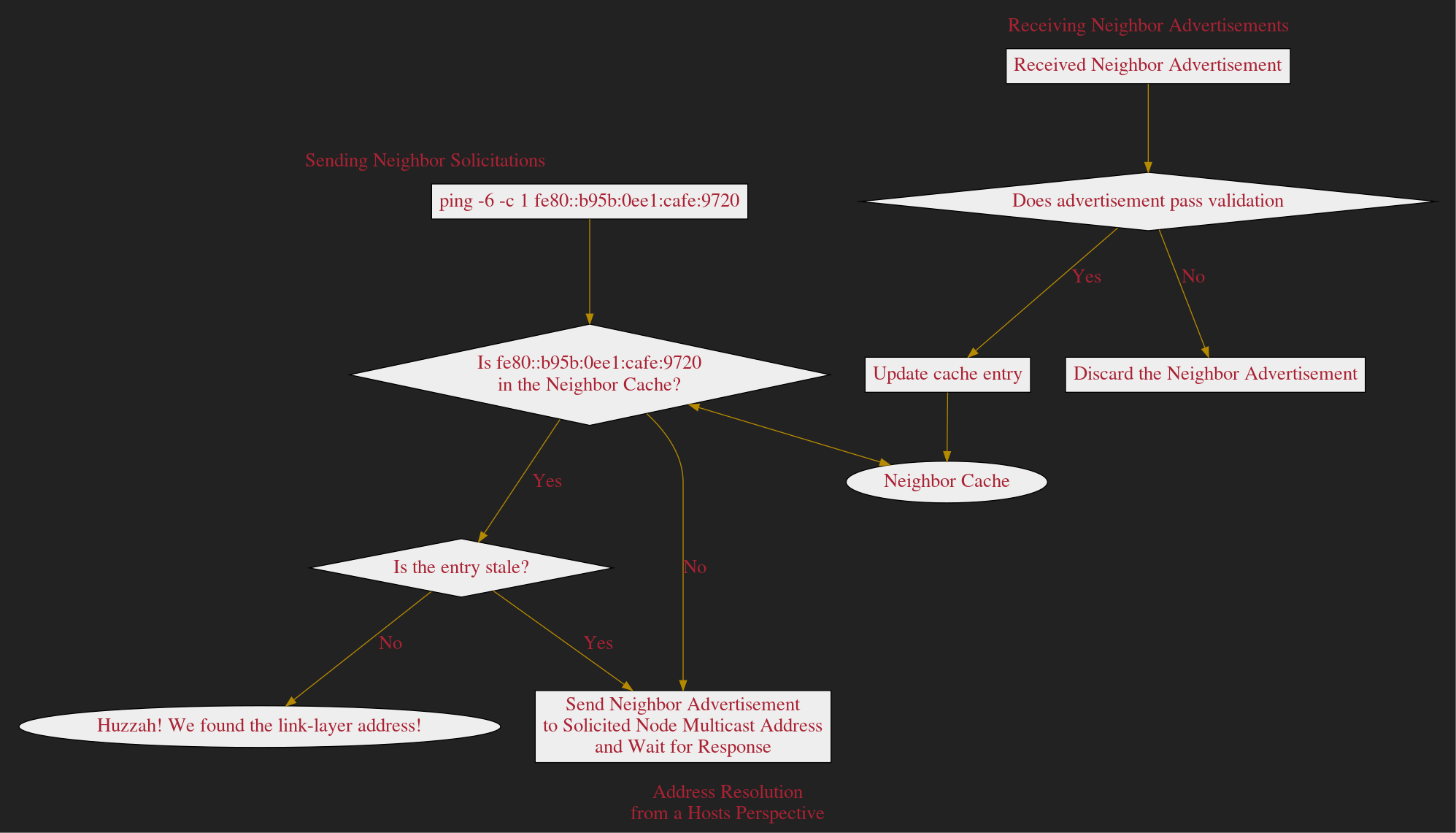
Address Resolution
Neighbor Advert/Solicit
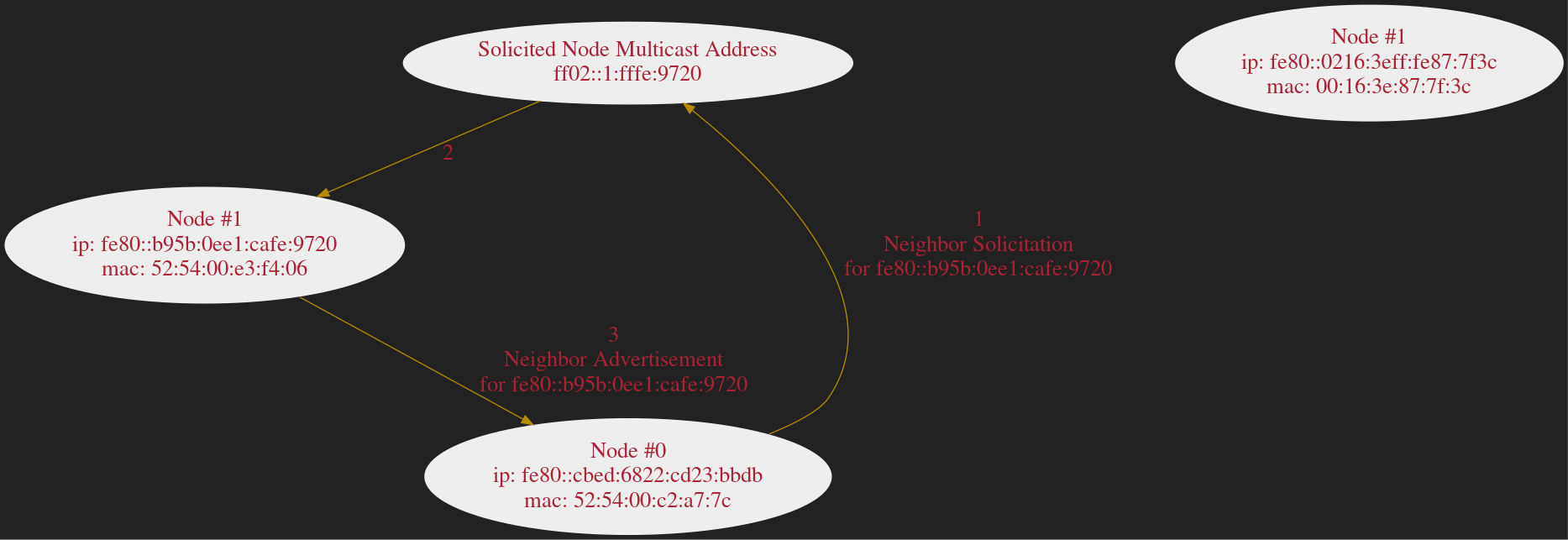
Neighbor Cache
Neighbor Cache Poisoning
| Host | IPv6 Address | Link-layer Address |
|---|---|---|
| Node #0 | fe80::cbed:6822:cd23:bbdb | 52:54:00:c2:a7:7c |
| Node #1 | fe80::b95b:0ee1:cafe:9720 | 52:54:00:e3:f4:06 |
| Attacker | fe80::0216:3eff:fe87:7f3c | 00:16:3e:87:7f:3c |
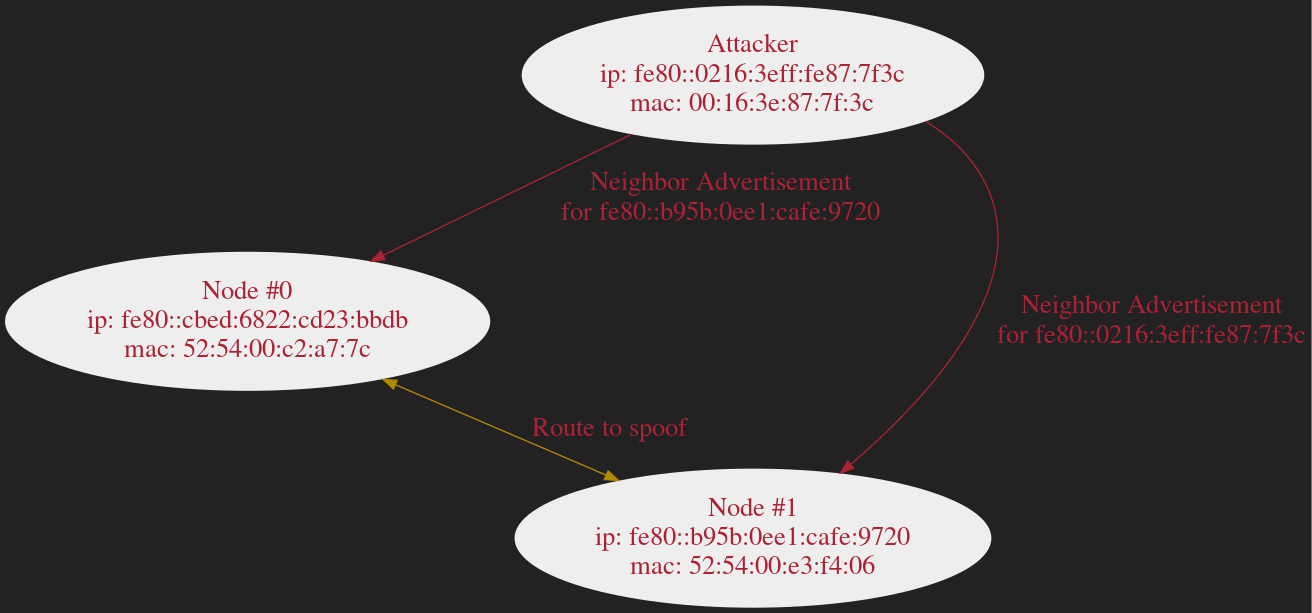
Ethernet II, Src: Xensourc_87:7f:3c (00:16:3e:87:7f:3c), Dst: RealtekU_c2:a7:7c (52:54:00:c2:a7:7c)
Internet Protocol Version 6, Src: fe80::b95b:ee1:cafe:9720, Dst: fe80::cbed:6822:cd23:bbdb
Internet Control Message Protocol v6
Type: Neighbor Advertisement (136)
Code: 0
Checksum: 0x8a7f [correct]
[Checksum Status: Good]
Flags: 0x20000000, Override
0... .... .... .... .... .... .... .... = Router: Not set
.0.. .... .... .... .... .... .... .... = Solicited: Not set
..1. .... .... .... .... .... .... .... = Override: Set
...0 0000 0000 0000 0000 0000 0000 0000 = Reserved: 0
Target Address: fe80::b95b:ee1:cafe:9720
ICMPv6 Option (Target link-layer address : 00:16:3e:87:7f:3c)
Type: Target link-layer address (2)
Length: 1 (8 bytes)
Link-layer address: Xensourc_87:7f:3c (00:16:3e:87:7f:3c)Router Discovery
Active Aquisition of the Default Route
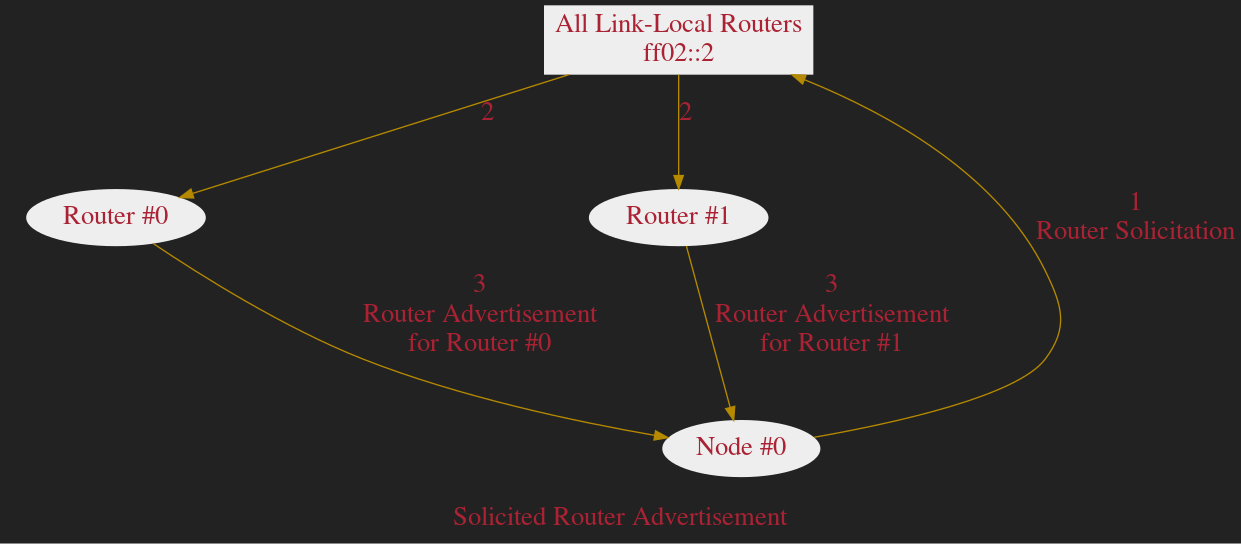
Passive Aquisition of the Default Route
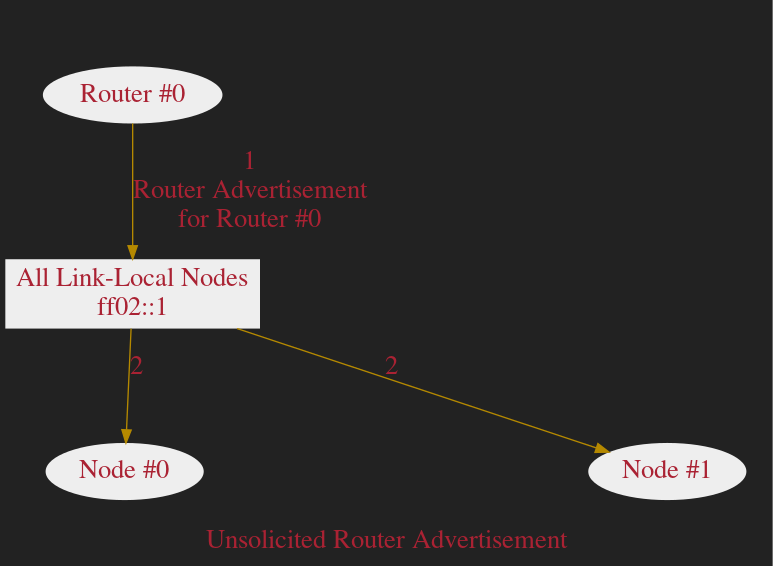
Hijacking the Default Route
Whenever the Lifetime of an entry in the Default Router List expires, that entry is discarded.
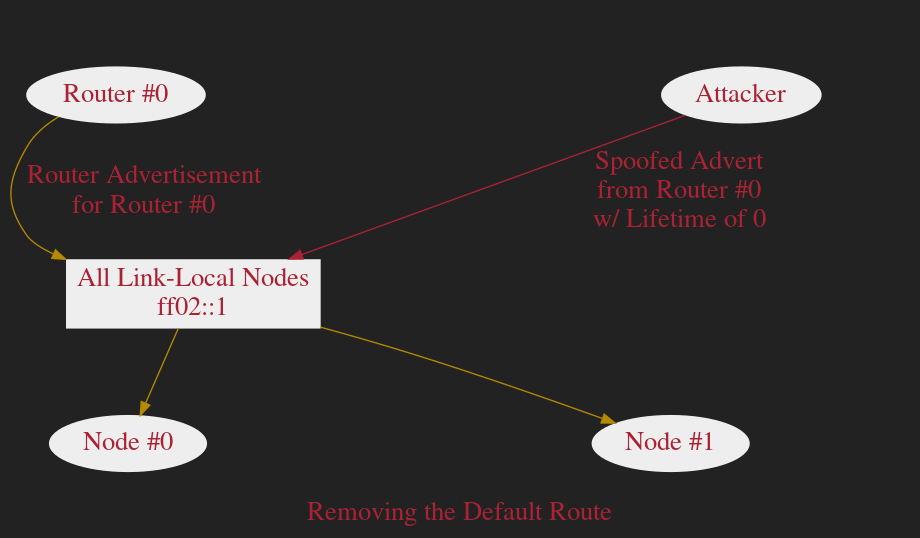
Ethernet II, Src: RealtekU_c2:a7:7c (52:54:00:c2:a7:7c), Dst: IPv6mcast_01 (33:33:00:00:00:01)
Internet Protocol Version 6, Src: fe80::cbed:6822:cd23:bbdb, Dst: ff02::1
Internet Control Message Protocol v6
Type: Router Advertisement (134)
Code: 0
Checksum: 0xc5ce [correct]
[Checksum Status: Good]
Cur hop limit: 255
Flags: 0x00, Prf (Default Router Preference): Medium
0... .... = Managed address configuration: Not set
.0.. .... = Other configuration: Not set
..0. .... = Home Agent: Not set
...0 0... = Prf (Default Router Preference): Medium (0)
.... .0.. = Proxy: Not set
.... ..0. = Reserved: 0
Router lifetime (s): 0
Reachable time (ms): 0
Retrans timer (ms): 0
ICMPv6 Option (Prefix information : fe80::cbed:6822:cd23:bbdb/64)
Type: Prefix information (3)
Length: 4 (32 bytes)
Prefix Length: 64
Flag: 0x00
0... .... = On-link flag(L): Not set
.0.. .... = Autonomous address-configuration flag(A): Not set
..0. .... = Router address flag(R): Not set
...0 0000 = Reserved: 0
Valid Lifetime: 0
Preferred Lifetime: 0
Reserved
Prefix: fe80::cbed:6822:cd23:bbdb
ICMPv6 Option (Source link-layer address : 52:54:00:c2:a7:7c)
Type: Source link-layer address (1)
Length: 1 (8 bytes)
Link-layer address: RealtekU_c2:a7:7c (52:54:00:c2:a7:7c)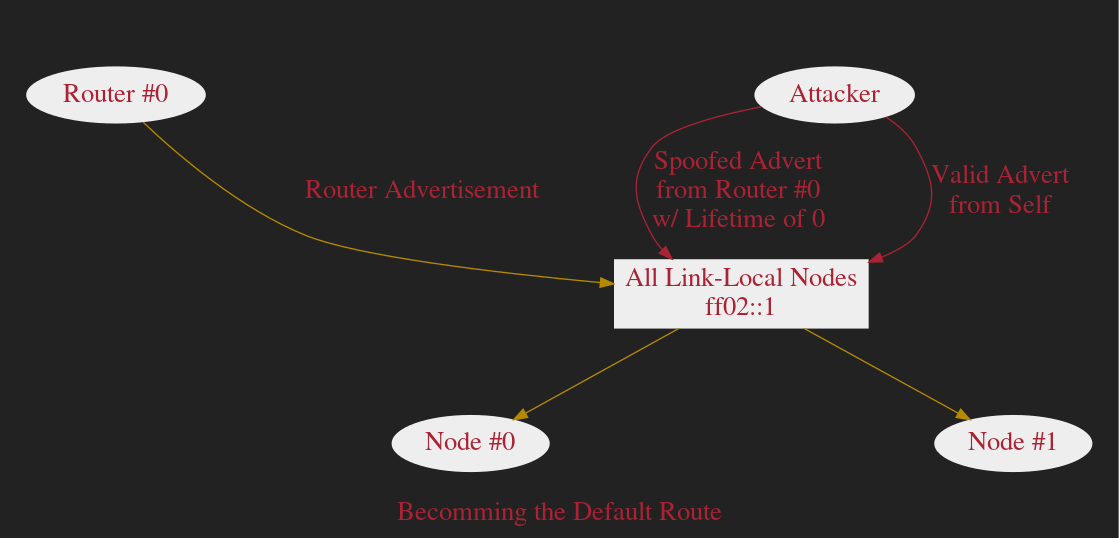
Using sylkie
Usage
- Command Line Tool
- Two basic subcommands
- Two options to streamline typical workflow
- C Library
Neighbor Advert
sylkie neighbor-advert \
-interface <interface> \
--dst-mac <dest hw addr> \
--src-ip <source ip> \
--dst-ip <dest ip address> \
--target-ip <target ip address> \
--target-mac <target mac address> \
--timeout <time betweeen adverts> \
--repeat <number of times to send the request>Router Advert
sylkie router-advert \
--interface <iterface> \
--target-mac <target mac> \
--router-ip <target ip> \
--prefix <prefix> \
--timeout <time betweeen adverts> \
--repeat <number of times to send the request>
We accept JSON!
sylkie -j </path/to/json>{
"router-advert": [
{
"interface": "<interface>",
"target-mac": "<target mac>",
"router-ip": "<router ip>",
"prefix": <prefix>,
"timeout": <number of times to send the request>,
}
],
"neighbor-advert": [
{
"interface": "<interface>",
"dst-mac": "<dest hw addr>",
"src-ip": "<source ip>",
"dst-ip": "<dest ip address>",
"target-mac": "<target mac address>",
"target-ip": "<target ip address>",
"timeout": <time betweeen adverts>,
}
]
}How we did it?
Normative References
Informative References
Practical References